Note: This blog is solely based on my work experience and research. This is NOT an official Cisco document. All the details and recommendations in this blog are my personal opinion.
As per Gartner’s definition, “SASE capabilities are delivered as a Service based upon the identity of the entity, real-time context, enterprise security/compliance policies and continuous assessment of risk/trust throughout the sessions.”
The word “Partner” also means “MSP” or “Managed Service Provider” in this blog.
For an end-customer the SASE capabilities has to deliver “as-a-Service”. The preferred approach to consume SASE capabilities is from a single vendor. Having said that, the Gartner report supports alternative approach to separate the “connect it” infrastructure from the “secure it” infrastructure of SASE. The only requirement common in both approaches is to have cloud-based services. So the question is,….The capabilities of SASE can only be delivered directly from a Vendor or it can delivered from a Partner in case of Managed Service model?.
Or in other words,
If a customer can consume SASE capabilities directly from the vendors and at the same time, the traditional product vendors are turning into service providers. What is the role of a Partner?
Good question !..
Customers (Enterprises) are on their journey to become a digital organization. Many customers have transformed most of their assets and business into digital to gain competitive advantage. To deal with the fast-changing industry landscape, customers use their IT to generate business value. For an Enterprise IT team, managing a hybrid digital infrastructure, the scale, the complexity and to provide business value, makes it a challenging task.
With SASE, customers can directly purchase and consume the capabilities from the vendors. But customer still owns the burden to manage and implement the SASE capabilities. Purchasing flexibility is one part of the puzzle, implementing and managing is the other part. This is where a Partner can add value.
There are mainly three ways SASE capabilities can be consumed as shown in the below Figure:1.
Note: You can purchase SASE services from re-sellers / distributers etc. I have limited the scope of the discussion to these three.

- Customer purchased SASE services directly from the vendor and it is managed by their own IT department.
- Customer purchased SASE services directly from the vendor and it is managed by an MSP on customer’s behalf.
- Customer purchased Managed SASE services from a Managed Service Provider(MSP).
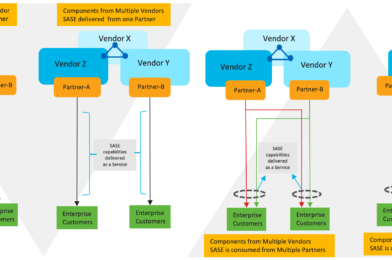
This blog is focused on the last bullet point. The Figure: 2 below shows you four different scenarios of delivering and consuming Managed SASE. The two scenarios in the left side has partner’s perspective and the right side has end-customer’s perspective.

From Left side,
Scenario 1— Partner using a single vendor to provide Managed SASE
Scenario 2 — Partner using multiple vendors to provide Managed SASE
Scenario 3 — Customer consumes multi-vendor Managed SASE from multiple Partners
Scenario 4 — Customer consumes single-vendor Managed SASE from multiple Partners
There are other scenarios where customer purchased SASE capabilities from one vendor/or multiple vendors and handed over the management to partner(s) on behalf of the customer. It is a whole different story and this blog does not cover those scenarios.
Scenario 1 — Partner using a single vendor to provide Managed SASE
Partner using a single vendor to create a manged offer to deliver SASE capabilities as-a-Service. SASE vendors may provide tools for managing multiple tenets, centralized setting & reports, flexible license and billing etc. Partner can focus on managing the SASE policies, provide support and usual operations. This is an ideal scenario.
Pros
One of the major reason to use single vendor is to reduce the cost and complexity.
Need not to hire headcounts for other vendor platforms. May able to manage with a focused team with expert skill set to deliver quality service.
Able to build good relationship with vendors to utilize loyalty based special discounts and programs.
Cons
May end up in vendor lock-in situation with not much choice.
Moving away from one vendor to another may take time and investment on resources and staff.
Limited options to create differentiated offers.
Scenario 2 — Partner using multiple vendors to provide Managed SASE
Partner uses multi-vendor SASE solutions to extend the SASE to end-customer as-a-Service. If managing the operational cost and complexity is feasible for an MSP/Partner then this model may provide a tad bit more advantage than a single vendor in my opinion.
Pros
Partner has the flexibility to choose best vendors from the market to put together a SASE offer
With multiple choice to select, Partner can negotiate the pricing with the vendors.
Mixing multiple vendors may open up new possibilities to create differentiated services.
Very less chances to be in a vendor lock-in situation
Cons
Need to handle different licensing terms and agreements with each vendors
Have to manage more than one portal or product console can add extra burden on existing staff. Need to invest resources in integrating and automating to achieve optimum results.
In case of break-fixing, in some situation engineers may need to coordinate with more than one vendor to resolve the issue. This may add significant delay to provide resolution and impact customer satisfaction.
Partners should have a mechanism to consolidate end-customers consumption (usage / metering) from multiple vendors in order to provide the monthly billing.
Scenario 3 — Customer consumes multi-vendor Managed SASE from multiple Partners
This scenario provides customer perspective. Like Partners, Customers have the flexibility to consume SASE capabilities from their choice of MSPs. If an MSP-A is best known for their connectivity services but not much into security services. Then customer can go with MSP-A for connectivity and choose another MSP for security services. In the end, Customer can enjoy the best of both worlds.
For example, MSP-A offers SD-WAN + Telemetry & Analytics as a package for connectivity, when compared with MSP-B’s simple SD-WAN only offer. Technical superiority in the offer led MSP-A to win the connectivity service. When it comes to security both MSPs provide very similar offer from one vendor so it may come down to the best pricing. Customer has chosen MSP-B for security, based on the offer pricing.
Pros
Flexibility for a customer to pick the MSP of their choice to deliver set of SASE capabilities as a service.
The competition between MSPs can help customers with the best offers and with a good price tag.
Cons
Add complexity to manage multiple partners and their service agreements . Make sure that the SLAs from all the vendors are similar.
In case of break-fix, especially in a high severity cases, vendors may ended-up pointing each other than working together to find a fix.
Scenario 4 — Customer consumes single-vendor Managed SASE from multiple Partners
It is less likely that a customer would care more on the internal systems and the vendors choice of an MSP. In a Managed Service world the focus will be the reputation of an MSP and the quality of the offers they deliver.
Having said that, for the sake of an argument let me take an example to explain the scenario. Assume both the MSPs are using Cisco. If MSP-A provides connectivity services including VPN and MSP-B provides security service (Umbrella) then the end customer will have to install only one Cisco AnyConnect agent. AnyConnect agent on an endpoint can be used for VPN connectivity as well to re-direct DNS and Web traffic to Cisco Umbrella. If both MSPs were using different vendors then the customer will have to install more than one software agent on the endpoint.
Conclusion
Most partners may have concerns about losing their existing revenue generated from managing the legacy boxes. Especially, when the new service offers like SASE are moving towards cloud. With the change in the IT industry, the role of a partner may change as well.
As per Gartner report, it is clear that those MSPs who are stuck with managing boxes to keep IT On and only offer operational management for internal enterprise IT environment will fail to grow [1].
Well, let’s see this change as an opportunity. In fact, in my opinion, Managed Services + SASE combination is a match made in heaven. With this combination end-customer can enjoy the true experience of the SASE capabilities and its management fully delivered as-a-Service.
Reference
[1] https://blogs.gartner.com/rene-buest/2019/10/08/infrastructure-msps-offer-operational-management-internal-enterprise-environments-will-fail-grow/VCD