Cisco Umbrella is a security product for safe internet access. It is a cloud-delivered solution with lots of security features including DNS-Layer security, Web security, Cloud access security broker (CASB), Cloud Delivered Firewall etc. For more details please check this link.
Umbrella has different packages. A package is a set of Umbrella features bundled based on market, for easy pricing and selling purpose. There are different packages for each segment of market, such as, Packages for Service Providers(SP) — Easy Protect, and Mobile Protect. Packages for Enterprise — DNS Essential, DNS Advantage and SIG Essential. Packages for Managed Service Providers (MSP), Packages for Managed Security Service Providers (MSSP), OpenDNS Home and Small business packages — OpenDNS Family Shield (Free) & OpenDNS Home (Free), OpenDNS VIP Home, OpenDNS Umbrella Prosumer etc.
For more details on package and comparison, please check below links
Cisco Umbrella Package Comparison
Cisco package comparison for Service providers & Distributors
Cisco OpenDNS Family and Small Business packages
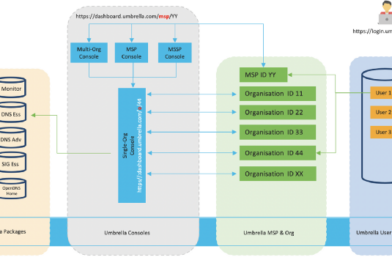
Before we talk about different Umbrella consoles, we need to understand how a user account is mapped to an Umbrella packages. Figure: 1 illustrates a logical flow of a user account accessing a package.
Note: This is not an official Cisco diagram. Diagram is only for discussion purpose and may not reflect the actually infrastructure.

A username can assign access privileges to one or more than one Umbrella organization (Org). An Org is an instance of Umbrella and has its own dashboard. Orgs are identified by their name and their organization ID (Org ID). The Org ID is a unique seven-digit number.
Dashboard is a GUI (Graphical User Interface) to interact with the Org instances. Other than dashboard for each Org, Cisco provides Console, a GUI tool to manage multiple organisations through a single instance of the console. There are few variants of consoles. Though they have very similar GUI but the features will be slightly different on each console.
MSSP (Managed Security Service Provider) Console

MSSP console typically for large service providers focused on managed security services for enterprises with security expertise. Usually they have customers with more than 250 employees or more to protect. MSSP Console main features includes centralised Customer Management & Reporting, able to manage Customer & license (MSLA &Term-based), Provide Trials, monitor, convert customers from trial to subscription and centralised configuration settings.
To get started with the MSSP console, first the service provider/partner has to determine Umbrella licensing and then add customer accounts. Service providers/partners have to two license type available on behalf of a customer.
- Term/GPL (Global Price List) — Term licenses are procured through CCW and owned by the customer. Licenses are sold to you ahead of time.
- MSLA — Managed Service License Agreement. A volume-based monthly, post-paid billing model for Managed Service Providers of any kind: MSP, MSSP, or ISPs. Licenses are issued when a customer account is added by the MSSP and at the end of each month Cisco bills you based on the number of licenses — customers added — during that thirty day period. There is no minimum or maximum number of licenses.
- Both — Allows you the option of selecting either Term or MSLA when adding a new customer account.
Please check the link for more details on MSSP requirements for a partner to access MSSP console.
MSP (Manged Service Provider) Console

MSP console are designed for service providers who manages IT services on behalf of a customer. They have fewer than 250 employees to protect per customer. Their security requirements may not complex like MSSP customers. MSP customers may have simple security need to defend them from threats like malware, phishing, ransomware etc. MSP console’s main feature includes centralised Customer Management, Setting & Reporting. Also the console is designed to integrate with the Connectwise and AutoTask PSAs. Also provides you with the information you need to deploy through a Remote Monitoring and Management (RMM) tool.
Unlike MSSP, MSPs can purchase a bucket of seats to allocate and reallocate those seats to customers as best fits their business needs. Because the license is typically blended into a managed service provided by the MSP, it’s owned by the MSP and not the customer.
Umbrella Partner Console (UPC)

UPC is more of a trail management tool. The console is designed for service providers/partners to set up and manage customer free trials and in the end of the trail, provide them with reports showing the threats and vulnerabilities that Umbrella was able to detect and mitigate during their free trial. UP Console feature includes Centralised Reports & Setting and Trail Management.
Please check the link for more details on UPC eligibility.
Mult-Org Console

Multi-org console is not designed for service providers but for an large enterprise. This console is suitable for organisations that are highly distributed but share a common IT group or network security team. As per Umbrella documentation — The Multi-org console is a good fit for these types of organisations: ones divided in structure but with a centralized security team that ensures compliance across all areas. The Console feature includes Centralised Reports & Settings and Org Management. A customer has to purchase separate license for Multi-Org console.
Conclusion
MSSP Console is for large Service Providers/Partners focused on Security managed services.
MSP Console is for small IT managed service providers who manages IT infrastructure behalf of their customer.
UP Console is for Partners to help with Umbrella trail management.
Multi-Org Console is for large enterprise to managed their internal distributed sub-orgs.